I was recently tasked with setting up a test environment to verify if it is possible to run the latest HAProxy with an up-to-date OpenSSL version and still support DES ciphers such as DES-CBC3-SHA.
While the use of a docker container with Ubuntu 16.04 and an old HAProxy paired with OpenSSL 1.0.2 would be an option, the whole stack would be heavily outdated. Therefore, to support DES-CBC3-SHA with TLSv1.0 (for example for incoming connections from Windows Server 2003, where the last supported cipher is exactly the one named above) a suitable solution can be a manually compiled haproxy with OpenSSL 3.0.
Compile OpenSSL for local testing:
wget https://www.openssl.org/source/openssl-3.0.9.tar.gz
tar -xf openssl-3.0.9.tar.gz
cd openssl-3.0.9/
mkdir sc sc1
./config --prefix=/home/user/Schreibtisch/openssl-3.0.9/sc --openssldir=/home/user/Schreibtisch/openssl-3.0.9/sc1 no-shared enable-weak-ssl-ciphers -DOPENSSL_TLS_SECURITY_LEVEL=0 enable-des -Wl,-rpath=/home/user/Schreibtisch/openssl-3.0.9/sc/lib64
make -j $(nproc)
make install
Using the command “sc/bin/openssl ciphers -s -V ALL | grep DES” you can now verify if the openssl library supports the cipher named above:
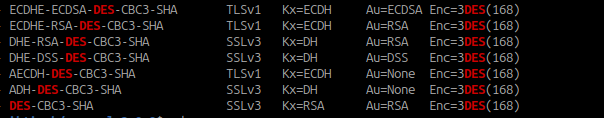
$ sc/bin/openssl ciphers -s -V ALL | grep DES
0xC0,0x08 - ECDHE-ECDSA-DES-CBC3-SHA TLSv1 Kx=ECDH Au=ECDSA Enc=3DES(168) Mac=SHA1
0xC0,0x12 - ECDHE-RSA-DES-CBC3-SHA TLSv1 Kx=ECDH Au=RSA Enc=3DES(168) Mac=SHA1
0x00,0x16 - DHE-RSA-DES-CBC3-SHA SSLv3 Kx=DH Au=RSA Enc=3DES(168) Mac=SHA1
0x00,0x13 - DHE-DSS-DES-CBC3-SHA SSLv3 Kx=DH Au=DSS Enc=3DES(168) Mac=SHA1
0xC0,0x17 - AECDH-DES-CBC3-SHA TLSv1 Kx=ECDH Au=None Enc=3DES(168) Mac=SHA1
0x00,0x1B - ADH-DES-CBC3-SHA SSLv3 Kx=DH Au=None Enc=3DES(168) Mac=SHA1
0x00,0x0A - DES-CBC3-SHA SSLv3 Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1
Compile HAProxy 2.8 with the OpenSSL compiled prior:
wget https://www.haproxy.org/download/2.8/src/haproxy-2.8.0.tar.gz
tar -xf haproxy-2.8.0.tar.gz
cd haproxy-2.8.0
make -j $(nproc) TARGET=linux-glibc USE_OPENSSL=1 SSL_INC=/home/user/Schreibtisch/openssl-3.0.9/sc/include SSL_LIB=/home/user/Schreibtisch/openssl-3.0.9/sc/lib64 LDFLAGS="-Wl,-rpath,/home/user/Schreibtisch/openssl-3.0.9/sc/lib64"
In your haproxy source directory you will now find a ELF binary “haproxy”, which you can run with the “-vv” parameter to see if the correct OpenSSL library is being used (“./haproxy -vv”):
Built with OpenSSL version : OpenSSL 3.0.9 30 May 2023
Running on OpenSSL version : OpenSSL 3.0.9 30 May 2023
Using the HAProxy binary with its statically linked OpenSSL, you can now set up endpoints with SSL and DES-CBC3-SHA cipher support.
Of course, to finish this task properly, you would now go ahead and somehow package this binary with some kind of config file.